2023SharkCTF-week3-Reverse-wp
2023SharkCTF-week3-Reverse-wp
2023.9.16 by Shen_Fan
第三周的题大多是烂活,还请各位佬轻喷
Encrypted_Code
运行后是个平平无奇的flag检查程序,扔ida里看一眼
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
可以看到程序读入一个字符串到v4,然后将v4作为loc_401550的参数进行函数调用,再根据unk_408970的值进行判断。
对unk_408970进行交叉引用查询发现无其他引用,且loc_401550处是依托乱码,代码可能被加密。使用ida进行动态调试得到loc_401550解密后的代码
1 | _DWORD *__fastcall sub_401550(__int64 a1) |
简单的异或,编写脚本如下:
1 |
|
得到结果
1 | sharkctf{sEEms_YOU_KNOw_HOW_7O_dE8uG_tH1$_PRoGr4me!! |
拼接得到最终flag:
1 | sharkctf{sEEms_YOU_KNOw_HOW_7O_dE8uG_tH1$_PRoGr4me!!_0xdeadbeaf} |
Find_Bomb_Plus
解法1:
直接扫雷得到flag(有一定概率可以不猜直接扫出)
解法2:
通过动态调试直接找到雷的位置然后解出
解法3:
通过ida进行patch更改地图大小为1*21,一发入魂
flag就交给你们自己去找了
shell
扔到die里一看,upx,还被modified了,手动脱一手壳
这里使用的工具是x64dbg
F9越过库函数后来到这里
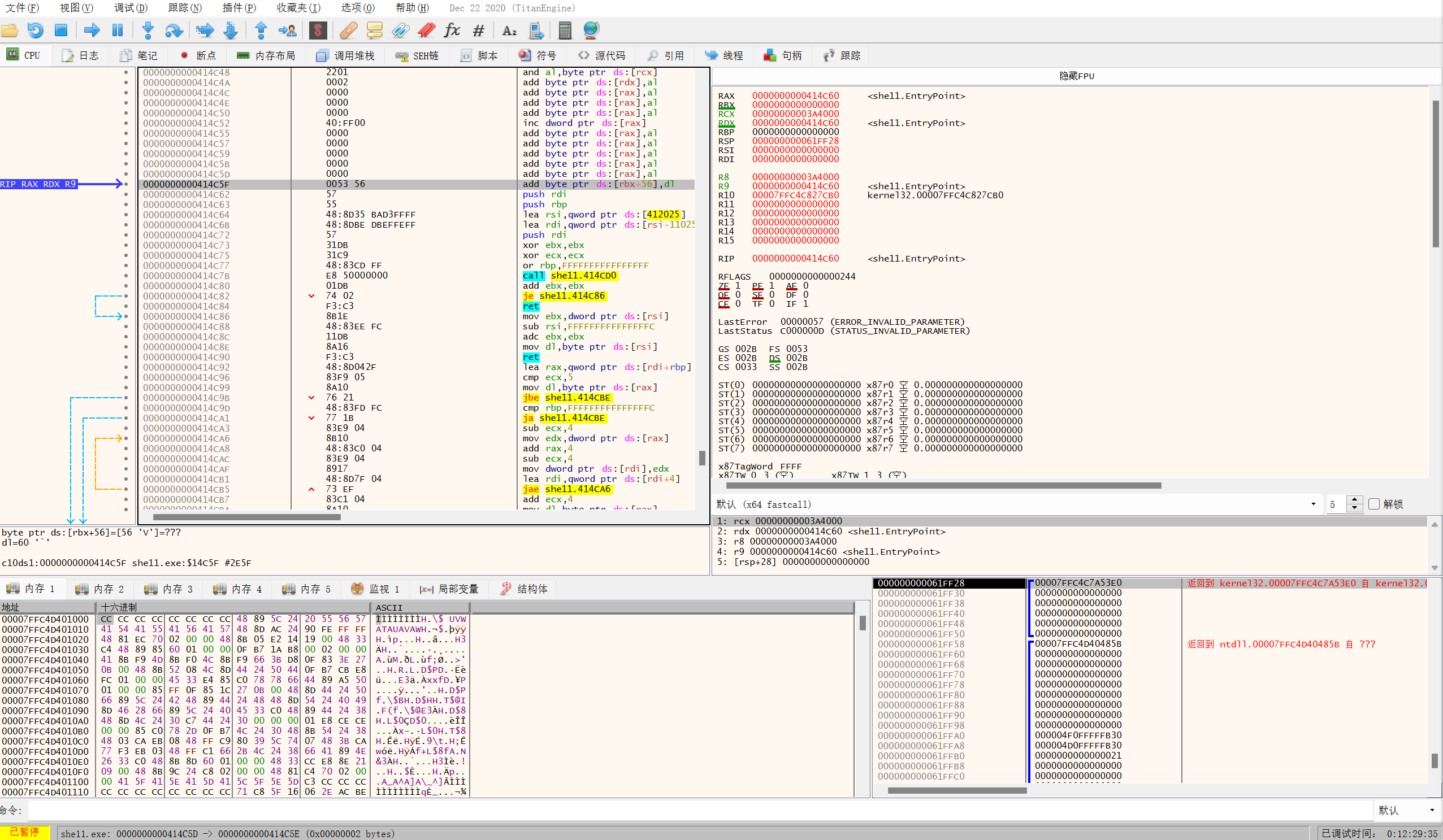
根据esp定理,在这里某一次push后在内存对应位置下硬件断点
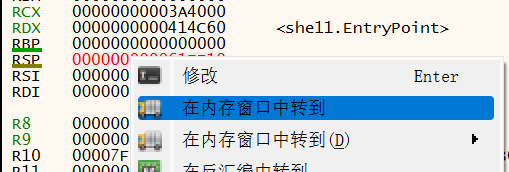
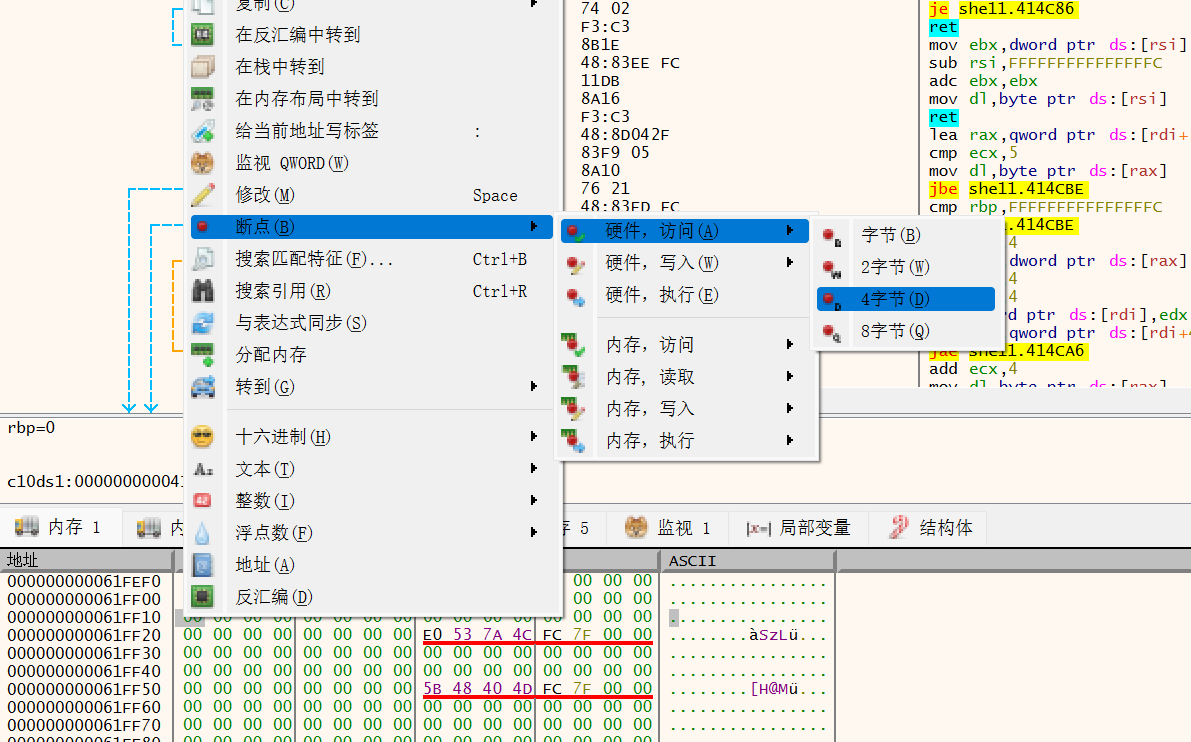
然后F9开始运行直到断点被触发
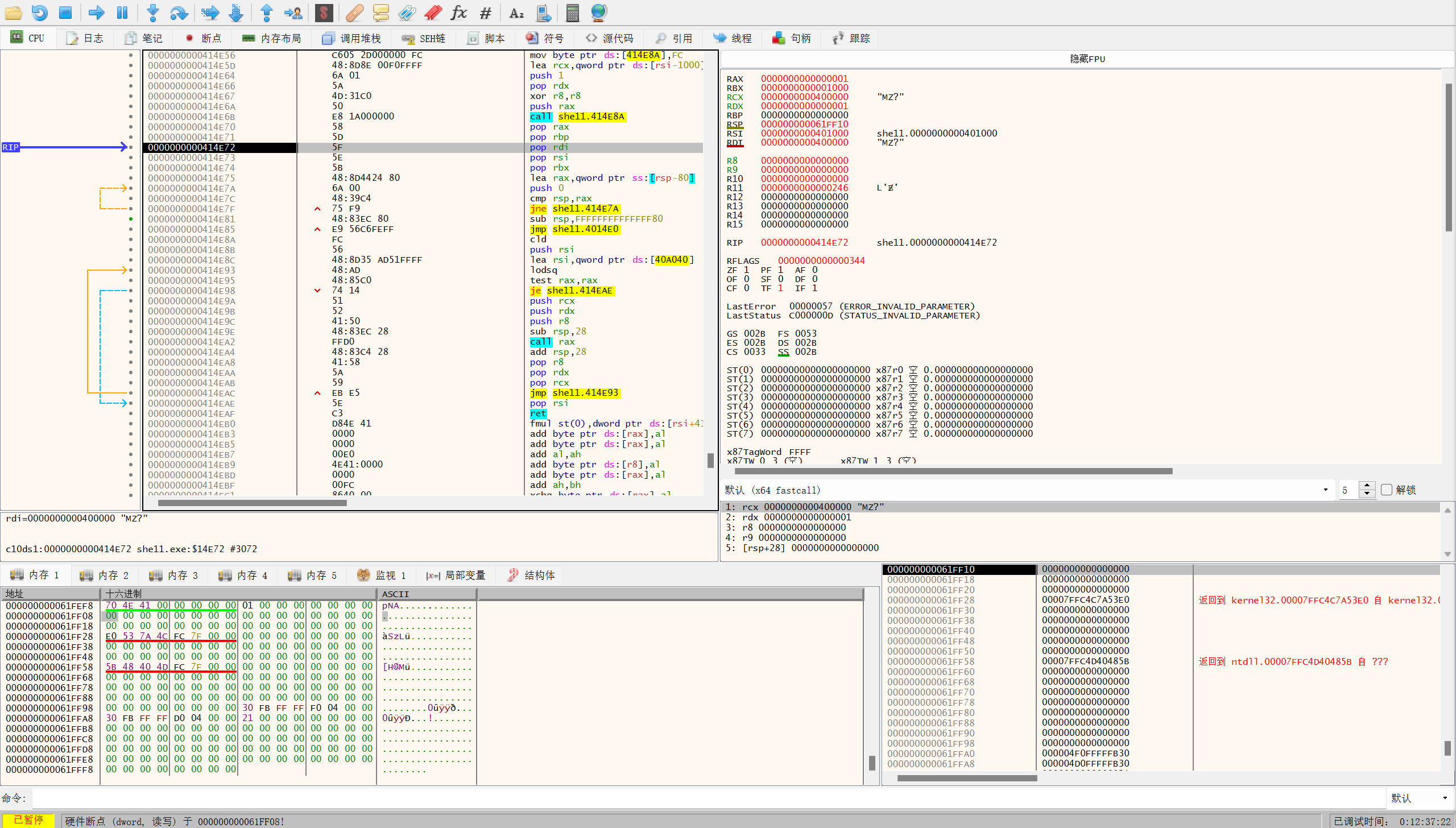
待pop完成后使用插件Scylla进行dump
将dump后的程序丢入ida后根据字符串”flag:”找到main函数
对逻辑分析后鉴定为rc4,编写脚本解密
1 |
|
得到flag:
1 | sharkctf{upX_@Nd_RC4_15_fuN} |
Star_Rail
如果说扫雷还能扫出来,那么这个是真抽不出来了(悲
使用ida64打开,虽然能找到输出flag的函数,但函数被加花了ida无法直接分析。
根据平时的经验,对随机数判断部分进行patch来逆天改命
1 | for ( i = 0; i <= 9; ++i ) |
可以看到若v4为0或1,即可输出金光,直接根据汇编将此判断改为100
以下是详细过程:
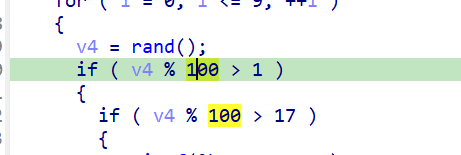
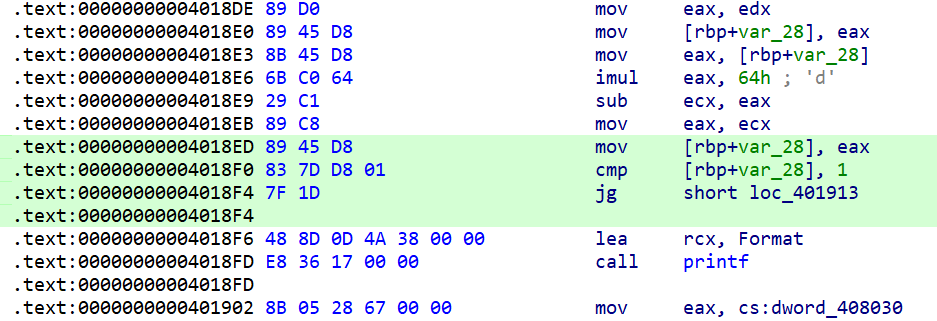
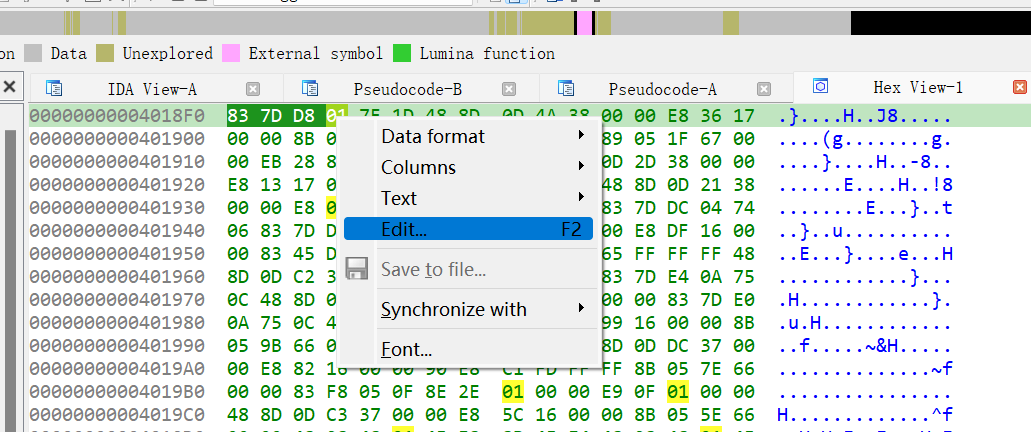
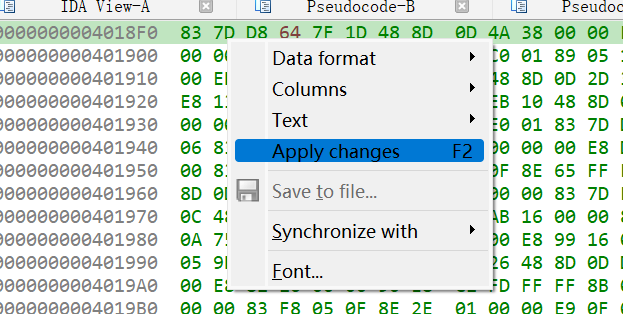
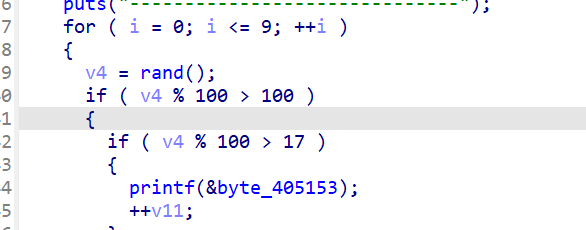
然后在ida中Edit->Patch programe->Apply patched to…将patch覆盖到原程序文件
运行一键得到flag